Federal Investigation: Office365 Data Breaches Result In Multi-Million Dollar Loss
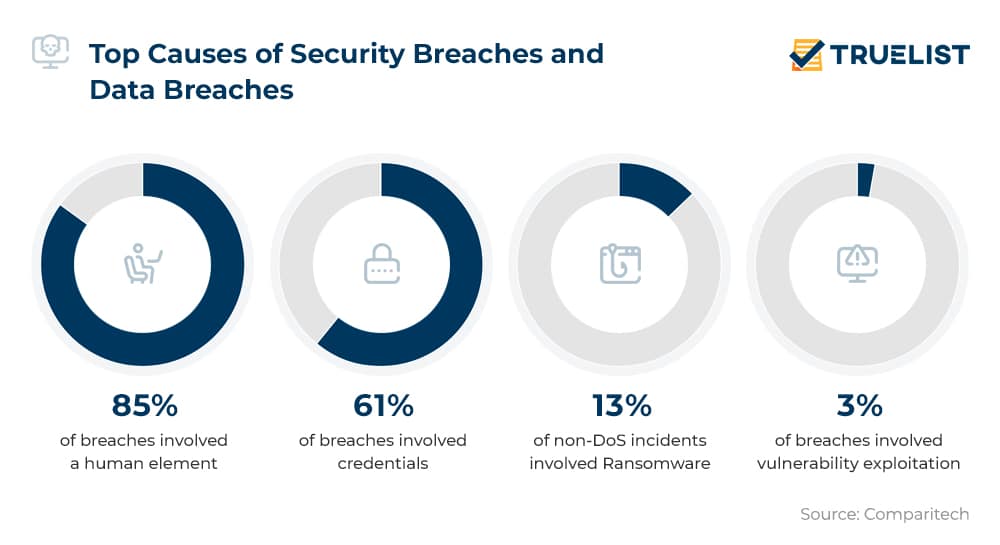
Table of Contents
Understanding the Vulnerabilities in Office365 Leading to Data Breaches
Office365, while a powerful productivity tool, presents several vulnerabilities that malicious actors can exploit. Understanding these weaknesses is the first step towards effective protection.
Phishing and Social Engineering Attacks
Sophisticated phishing campaigns represent a major threat to Office365 security. Cybercriminals craft convincing emails, often mimicking legitimate organizations or individuals, to trick users into revealing sensitive information or clicking malicious links.
- Spear phishing: Highly targeted attacks focusing on specific individuals within an organization, often using personally identifiable information to increase their credibility.
- Whaling: A type of spear phishing targeting high-profile executives or other key personnel.
- Consequences: Successful phishing attacks can lead to account compromise, malware infections, data theft, and significant financial losses. For example, a successful whaling attack could result in fraudulent wire transfers or the compromise of sensitive business strategies.
Compromised Credentials and Password Vulnerabilities
Weak or reused passwords are a significant security risk. Cybercriminals employ various techniques to exploit these vulnerabilities:
- Credential stuffing: Using stolen credentials from other breaches to attempt to access Office365 accounts.
- Brute-force attacks: Using automated tools to try numerous password combinations until a match is found.
- Importance of MFA: Multi-factor authentication (MFA) adds an extra layer of security, requiring users to provide multiple forms of verification before accessing their accounts. This significantly reduces the risk of unauthorized access, even if credentials are compromised.
Third-Party Application Vulnerabilities
Integrating third-party applications with Office365 enhances functionality but also introduces security risks.
- Vetting third-party apps: It's crucial to thoroughly vet any third-party application before integrating it with Office365, ensuring it meets stringent security standards.
- Malicious apps: Malicious apps can be designed to steal data, install malware, or disrupt operations.
- API Security: Secure APIs are essential to prevent unauthorized access to data through third-party integrations.
Insider Threats and Malicious Actors
Even employees can pose a threat, either intentionally or unintentionally.
- Malicious intent: Employees with malicious intent can steal data or cause damage to the organization's systems.
- Employee training: Comprehensive security awareness training is essential to mitigate this risk.
- Data Loss Prevention (DLP) tools: These tools monitor and prevent sensitive data from leaving the organization, even through unauthorized channels. Access control measures must be enforced diligently.
The Financial Ramifications of Office365 Data Breaches
The financial consequences of an Office365 data breach can be devastating, impacting both directly and indirectly.
Direct Costs: Remediation, Legal Fees, and Regulatory Fines
- Incident response: The cost of investigating a breach, containing the damage, and recovering data can be substantial.
- Legal fees: Legal fees associated with responding to lawsuits, regulatory investigations, and notifications to affected individuals can be extremely high.
- Regulatory fines: Non-compliance with regulations like GDPR and CCPA can result in massive fines. The cost varies depending on the severity of the breach and the affected data.
Indirect Costs: Reputational Damage, Loss of Customers, and Business Disruption
- Reputational damage: A data breach can severely damage a company's reputation, leading to loss of customer trust and brand value.
- Loss of customers: Customers may switch to competitors due to concerns about data security.
- Business interruption: A breach can disrupt business operations, leading to lost productivity and revenue.
Federal Investigations and Their Consequences
Federal agencies like the FTC and DOJ investigate significant data breaches.
- Legal implications: Failing to comply with data breach notification laws can result in significant penalties.
- Penalties: Penalties can include substantial fines, legal action, and reputational damage.
Mitigating the Risk of Office365 Data Breaches
Proactive security measures are crucial in preventing costly Office365 data breaches.
Implementing Robust Security Measures
- Password management and MFA: Enforce strong password policies and implement MFA for all accounts.
- Advanced threat protection: Utilize advanced threat protection tools to detect and prevent malicious activity.
- Security audits and vulnerability assessments: Regularly conduct security audits and vulnerability assessments to identify and address weaknesses.
Employee Training and Security Awareness Programs
- Phishing and social engineering training: Educate employees on how to recognize and avoid phishing attempts and social engineering tactics.
- Regular security awareness training: Conduct regular training sessions to keep employees up-to-date on the latest security threats.
- Simulated phishing campaigns: Use simulated phishing campaigns to test employee awareness and identify vulnerabilities.
Data Loss Prevention (DLP) and Access Control Strategies
- DLP tools: Implement DLP tools to monitor and prevent sensitive data from leaving the organization.
- Least privilege access control: Grant employees only the access they need to perform their jobs.
- Regular access reviews and audits: Regularly review and audit user access permissions to ensure they are appropriate and up-to-date.
Conclusion: Protecting Your Business from Costly Office365 Data Breaches
Office365 data breaches present significant financial and legal risks. The vulnerabilities discussed – from phishing attacks to compromised credentials and insider threats – highlight the need for a proactive and multi-layered security approach. Implementing robust security measures, providing comprehensive employee training, and utilizing data loss prevention tools are critical for preventing costly data breaches and avoiding the potential for multi-million dollar losses and federal investigations. Don't wait for a breach to occur; take action now to protect your organization. Learn more about strengthening your Office365 security by exploring [link to relevant resource/service].

Featured Posts
-
 Latest Mets News Neuse Optioned Megills Return To Rotation
Apr 28, 2025
Latest Mets News Neuse Optioned Megills Return To Rotation
Apr 28, 2025 -
 Market Volatility When Professionals Sell Individuals Buy A Case Study
Apr 28, 2025
Market Volatility When Professionals Sell Individuals Buy A Case Study
Apr 28, 2025 -
 World Famous Chefs Fishermans Stew Receives Rave Review From Eva Longoria
Apr 28, 2025
World Famous Chefs Fishermans Stew Receives Rave Review From Eva Longoria
Apr 28, 2025 -
 Will Aaron Judge Bat Leadoff Analyzing Boones Lineup Decisions
Apr 28, 2025
Will Aaron Judge Bat Leadoff Analyzing Boones Lineup Decisions
Apr 28, 2025 -
 10 Gb Data Sim Card For Uae Includes 15 Abu Dhabi Discount
Apr 28, 2025
10 Gb Data Sim Card For Uae Includes 15 Abu Dhabi Discount
Apr 28, 2025
